Errata exists for this version of the document.
In addition, each Application Instance Certificate has a private key which should be stored in a location that can only be accessed by the application. If this private key is compromised, the administrator shall assign a new Application Instance Certificate and private key to the application.
This Certificate may be generated automatically when the application is installed. In this situation the private key assigned to the Certificate shall be used to create the Certificate signature. Certificates created in this way are called self-signed Certificates .
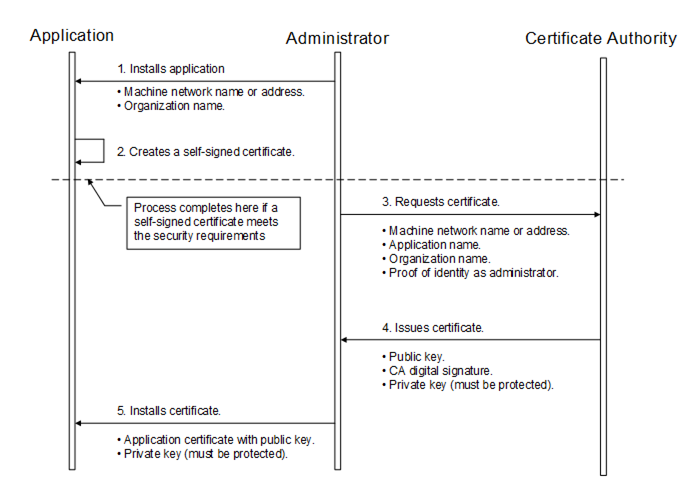
If the administrator responsible for the application decides that a self-signed Certificate does not meet the security requirements of the organisation, then the administrator should install a Certificate issued by a Certification Authority . The steps involved in requesting an Application Instance Certificate from a Certificate Authority are shown in Figure 19 .

The figure above illustrates the interactions between the application, the Administrator and the Certificate Authority . The Application is as OPC UA Application installed on a single machine. The Administrator is the person responsible for managing the machine and the OPC UA Application . The Certificate Authority is an entity that can issue digital Certificates that meet the requirements of the organisation deploying the OPC UA Application .
If the Administrator decides that a self-signed Certificate meets the security requirements for the organisation, then the Administrator may skip Steps 3 through 5. Application vendors shall ensure that a Certificate is available after the installation process. Every OPC UA Application shall allow the Administrators to replace Application Instance Certificates with Certificates that meet their requirements.
When the Administrator requests a new Certificate from a Certificate Authority , the Certificate Authority may require that the Administrator provide proof of authorization to request Certificates for the organisation that will own the Certificate . The exact mechanism used to provide this proof depends on the Certificate Authority .
Vendors may choose to automate the process of acquiring Certificates from an authority. If this is the case, the Administrator would still go through the steps illustrated in Figure 19 , however, the installation program for the application would do them automatically and only prompt the Administrator to provide information about the application instance being installed.
Please report errors or issues with the site to webmaster.
Copyright © 2024 - OPC Foundation